Yes, I am studying for my CCNA exam which is coming very soon. So I am going to use this blog to take down my study note. Okay, let’s start with setting up a lab with some Cisco switches, Cisco routers and computer.
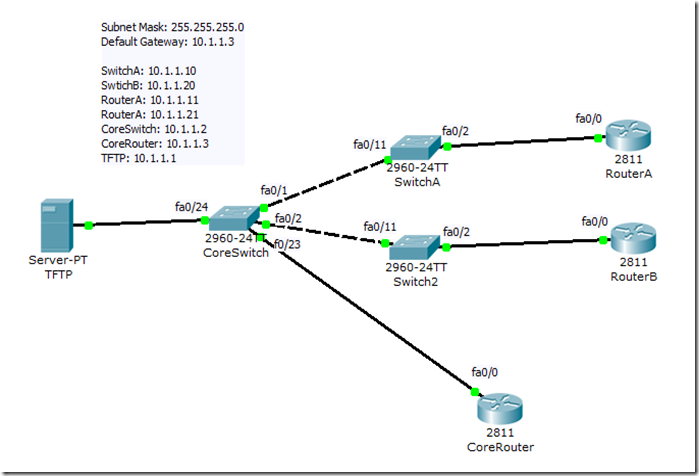
This is the lab that I have setup, 3 Cisco switches, 3 Cisco routers and 1 TFTP server using Cisco Packet Tracer.
I did the configuration for the routers first. The configuration for the 3 routers are pretty much the same except the IP address assigned, hostname and the description for the interface. Here is an example of how I configured the CoreRouter.
| Configuring the CoreRouter |
|
Configure the host name to CoreRouter. Router>enable Set sanfran as password for the privileged EXEC mode. CoreRouter(config)#enable secret sanfran Set the IP address for the router on interface fa0/0 and bring up the interface. CoreRouter(config)#interface fa0/0 Provide a description to the fa0/0 interface. CoreRouter(config-if)#description “CoreRouter to CoreSwitch” Set cisco as the password for the line console and sanjose as the password for the 5 vty lines (e.g. telnet). CoreRouter(config-if)#line console 0 Enable synchronous logging of messages for the console port to pipe system message under the command. CoreRouter(config)#line console 0 Verify the settings of interface fa0/0. Note down the MAC address of the interface fa0/0 when configuring RouterA and RouterB. The MAC address will be used for port-security configuration on SwitchA and SwitchB. CoreRouter(config-line)#end FastEthernet0/0 is up, line protocol is up (connected) Set the banner message. CoreRouter(config)#banner motd "Warning: Unauthorised access is not allowed" Save the running configuration to the NVRAM. Just hit Enter when asked for filename. CoreRouter#copy running-config startup-config Verify the running configuration and startup-configuration. CoreRouter#show running-config |
Next I did the configuration for the switches. The configuration of SwitchA, SwitchB and CoreSwitch is pretty much the same except of the IP address of the management VLAN interface (e.g. vlan1), hostname and description of interfaces.
| Configuring the SwitchA |
| Configure the host name to SwitchA. Switch>enable Set sanfran as password for the privileged EXEC mode. SwitchA (config)#enable secret sanfran Set the IP address for the switch on interface valn1 and bring up the interface. SwitchA (config)#interface vlan1 Set the default gateway for the switch. SwitchA(config)#ip default-gateway 10.1.1.3 Set the speed and duplex of interface fa0/11 to 100Mb/s and full duplex. SwitchA(config)#interface fa0/11 Provide a description to the fa0/11 interface. SwitchA(config-if)#description “SwitchA to CoreSwitch” Configure port security on interface fa0/2 to allow only Router A to be able to use this port. SwitchA(config-if)#interface fa0/2 Command explanation: Provide a description to the fa0/2 interface. SwitchA(config-if)#description “SwitchA to RouterA” Set cisco as the password for the line console and sanjose as the password for the 5 vty lines (e.g. telnet). SwitchA(config-if)#line console 0 Enable synchronous logging of messages for the console port to pipe system message under the command. SwtichA(config)#line console 0 Set the banner message. SwitchA(config)#banner motd "Warning: Unauthorised access is not allowed" As usual verify the setting of the interfaces. SwtichA#show interface fa0/11 Verify the port security settings on interface fa0/2. SwitchA#show port-security interface fa0/2 Save the running configuration to the NVRAM. Just hit Enter when asked for filename. SwitchA#copy running-config startup-config Verify the running configuration and startup-configuration. SwitchA#show running-config |
The setting of the TFTP is really very simple.
Finally we will need to verify the connectivity of this small setup.
On either SwitchA or SwitchB run the show cdp neighbors to display the Cisco Discovery Protocol updates received on interfaces fa0/2 and fa0/11.
Here is an example on Switch A.
SwitchA#show cdp neighbors
Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge
S - Switch, H - Host, I - IGMP, r - Repeater, P - Phone
Device ID Local Intrfce Holdtme Capability Platform Port ID
RouterA Fas 0/2 127 R C2800 Fas 0/0
CoreSwitch Fas 0/11 156 S 2960 Fas 0/1
Ping the RouterA and the TFTP server.
SwitchA#ping 10.1.1.11
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.11, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/28/31 ms
SwitchA#ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 17/50/63 ms
Perform the same testing on other routers and switches. If there is no connectivity issue, then you are done with lab 1-1.
Disclaimer: All settings and passwords used here are for study purpose.






No comments:
Post a Comment