You can use the port-security feature to restrict the number of maximum number of devices allowed to connect to a switchport or specify what devices are allowed to connect to the switchport. This is by checking against the MAC address of the connecting device.
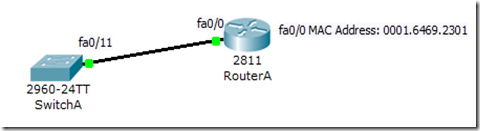
Let’s try this in the following simple setup. There is a SwitchA and RouterA. The MAC address of interface fa0/0 on RouterA is 0001.6469.2301. We are going to connect interface fa0/0 on RouterA to the interface fa0/11 on SwitchA. We are also going to restrict fa0/11 on SwitchA to only allow maximum 1 device to use the switchport and the MAC address of the device must be 0001.6469.2301.
So before connecting, we will enable port-security on interface fa0/11 of SwitchA.
SwitchA(config)#int f0/11
SwitchA(config-if)#switchport mode access
SwitchA(config-if)#switchport port-security
SwitchA(config-if)#switchport port-security maximum 1
SwitchA(config-if)#switchport port-security mac-address 0001.6469.2301
The switchport which is fa0/11 in this case must be in access mode to have port-security enabled and the command switchport mode access does that. The command switchport port-security enabled the port-security on fa0/11. The next 2 commands set the maximum number of connecting device allowed and the static MAC address of the allowed connecting device.
You can verify the port-security of fa0/11 using the sh port-security command.
SwitchA#sh port-security int f0/11
Port Security : Enabled
Port Status : Secure-down
Violation Mode : Shutdown
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 1
Configured MAC Addresses : 1
Sticky MAC Addresses : 0
Last Source Address:Vlan : 0000.0000.0000:0
Security Violation Count : 0
As shown, if there is a violation, the switchport will be shutdown. You can alter the violation action by using the switchport port-security violation command.
SwitchA(config-if)#switchport port-security violation ?
protect Security violation protect mode
restrict Security violation restrict mode
shutdown Security violation shutdown mode
The protect and restrict mode do not shutdown the port but will drop frames sending through the port.
Now, let’s connect RouterA and SwitchA.
If you check the MAC address on interface fa0/11, you will see the static MAC address 0001.6469.2301.
SwitchA#sh mac-address-table int f0/11
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1 0001.6469.2301 STATIC Fa0/11
The sh port-security command shows that the port status is secure-up.
SwitchA#sh port-security int f0/11
Port Security : Enabled
Port Status : Secure-up
Violation Mode : Shutdown
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 1
Configured MAC Addresses : 1
Sticky MAC Addresses : 0
Last Source Address:Vlan : 0001.6469.2301:1
Security Violation Count : 0
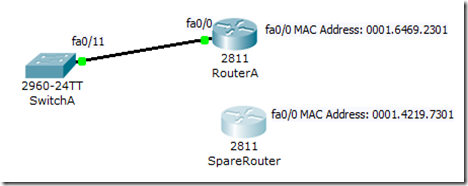
Now we introduced another router called SpareRouter. The MAC address of interface fa0/0 on SpareRouter is 0001.4219.7301.
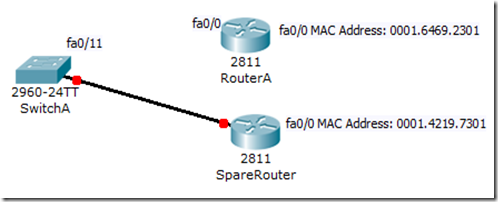
We are going to disconnect SwitchA and RouterA. We will then connect fa0/11 of SwitchA to fa0/0 of SpareRouter. Make sure the fa0/0 on SpareRouter is up by using the no shut command.
Once you connect up SwitchA and SpareRouter, you will see that the link is down.
%LINK-5-CHANGED: Interface FastEthernet0/11, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/11, changed state to up
%LINK-5-CHANGED: Interface FastEthernet0/11, changed state to administratively down
%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/11, changed state to down
Even if you tried to bring the interface fa0/11 up, it will still go down.
SwitchA(config)#int f0/11
SwitchA(config-if)#no shut
%LINK-5-CHANGED: Interface FastEthernet0/11, changed state to down
If you do sh int f0/11, you will see that the port is err-disabled.
SwitchA#sh int f0/11
FastEthernet0/11 is down, line protocol is down (err-disabled)
Hardware is Lance, address is 0001.43e8.ca0b (bia 0001.43e8.ca0b)
BW 100000 Kbit, DLY 1000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 100Mb/s
input flow-control is off, output flow-control is off
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:08, output 00:00:05, output hang never
Last clearing of "show interface" counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue :0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
956 packets input, 193351 bytes, 0 no buffer
Received 956 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
0 watchdog, 0 multicast, 0 pause input
0 input packets with dribble condition detected
2357 packets output, 263570 bytes, 0 underruns
0 output errors, 0 collisions, 10 interface resets
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier
0 output buffer failures, 0 output buffers swapped out
Check on the port-security of f0/11 and you will see that it is now in secure-shutdown state.
SwitchA#sh port-security int f0/11
Port Security : Enabled
Port Status : Secure-shutdown
Violation Mode : Shutdown
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 1
Configured MAC Addresses : 1
Sticky MAC Addresses : 0
Last Source Address:Vlan : 0001.4219.7301:1
Security Violation Count : 1
Okay, to bring the port up again, we need to first remove the connection to SpareRouter. Then we run shut to shutdown the fa0/11 interface on SwitchA and no shut to up the fa0/11 interface again.
SwitchA(config-if)#shut
%LINK-5-CHANGED: Interface FastEthernet0/11, changed state to administratively down
SwitchA(config-if)#no shut
%LINK-5-CHANGED: Interface FastEthernet0/11, changed state to down
Remember that the port-security on fa0/11 is still on. If you connect that port to another other device not having the MAC address specified, it will still err-disabled. If we connect it back to fa0/0 of RouterA, it will work again. If you really want to connect fa0/11 on SwitchA to other device, clear the port-security configuration and disabled port-security using the no version of the commands. For example, no switchport port-security.
There are other options you can set on the port-security. One of them is the sticky MAC address option. By using this option, you save the trouble of entering the MAC address manually.
SwitchA(config-if)#switchport port-security mac-address sticky
If we used this instead of switchport port-security mac-address 0001.6469.2301, the MAC address of the first connecting device will be learned. The MAC address of that device will be converted secure MAC address and added to the running configuration. Copying the running configuration to the startup configuration (e.g. copy run start), will save the learned MAC address to the start-up configuration file. If we reload the switch, the switch port does not need to relearn the MAC address.
Broadcast storm is coming, I need to find my spanning tree…






No comments:
Post a Comment