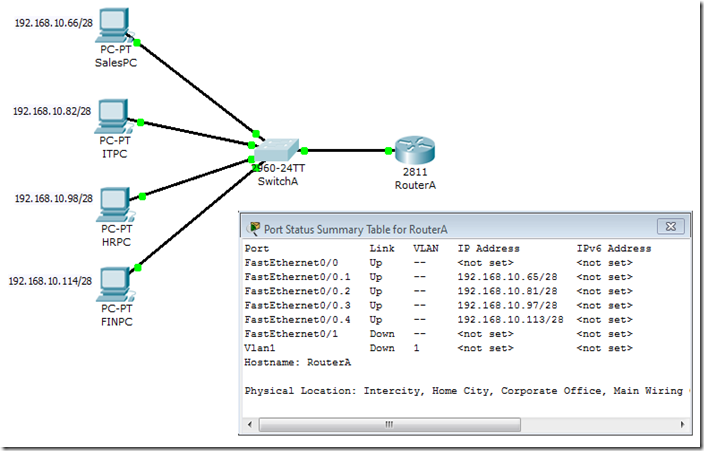
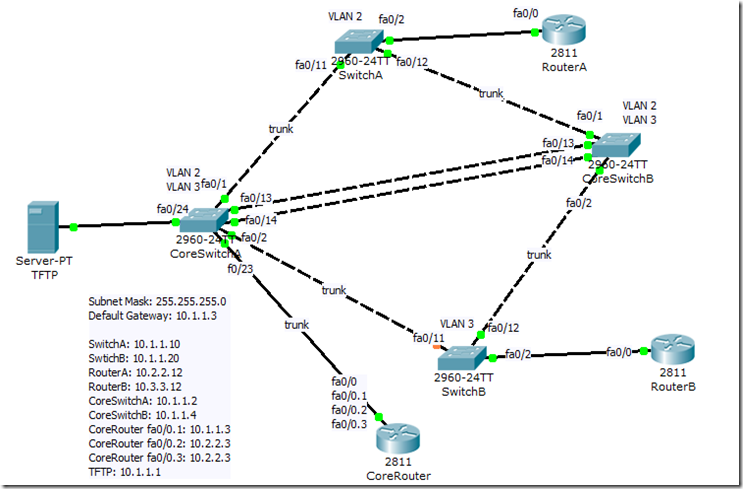
By default, EIGRP automatically summarizes routes at the classful boundary. However, we might want to turn it off for some cases such as having discontinuous networks. If we don’t disable automatic summarization for this case, the routers might not get the correct routing information. Here we will simulate such a case.

Continue from our previous setup of EIGRP, we have added a loopback 1 interface on RouterA and assign an IP address of 172.16.2.1 to it. We have also configure EIGRP on RouterA to advertise the loopback 1 network 172.16.0.0.
RouterA#sh ip protocols
Routing Protocol is "eigrp 100 "
Outgoing update filter list for all interfaces is not set
Incoming update filter list for all interfaces is not set
Default networks flagged in outgoing updates
Default networks accepted from incoming updates
EIGRP metric weight K1=1, K2=0, K3=1, K4=0, K5=0
EIGRP maximum hopcount 100
EIGRP maximum metric variance 1
Redistributing: eigrp 100
Automatic network summarization is in effect
Automatic address summarization:
192.168.1.0/24 for FastEthernet0/0, Serial0/0/1, Serial0/0/0, Loopback1
Summarizing with metric 128256
10.0.0.0/8 for Loopback0, Loopback1
Summarizing with metric 28160
172.16.0.0/16 for Loopback0, FastEthernet0/0, Serial0/0/1, Serial0/0/0
Summarizing with metric 128256
Maximum path: 4
Routing for Networks:
10.0.0.0
192.168.1.0
172.16.0.0
Routing Information Sources:
Gateway Distance Last Update
10.140.1.1 90 5377
10.23.23.2 90 7263
Distance: internal 90 external 170
Now if we try to ping 172.16.31.100 which is the loopback 0 interface on the CoreRouter using the source IP of loopback 1 interface on RouterA, it will fail.
RouterA#ping
Protocol [ip]:
Target IP address: 172.16.31.100
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 172.16.2.1
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.31.100, timeout is 2 seconds:
Packet sent with a source address of 172.16.2.1
UUUUU
Success rate is 0 percent (0/5)
Let’s check the routing table on RouterA and the CoreRouter to see what’s going on.
On RouterA
RouterA#sh ip route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 7 subnets, 2 masks
D 10.0.0.0/8 is a summary, 00:47:06, Null0
D 10.1.1.0/24 [90/2172416] via 10.140.1.1, 00:47:01, Serial0/0/0
C 10.2.2.0/24 is directly connected, FastEthernet0/0
D 10.3.3.0/24 [90/2172416] via 10.23.23.2, 00:46:59, Serial0/0/1
C 10.23.23.0/24 is directly connected, Serial0/0/1
C 10.140.1.0/24 is directly connected, Serial0/0/0
D 10.140.2.0/24 [90/2681856] via 10.140.1.1, 00:47:01, Serial0/0/0
[90/2681856] via 10.23.23.2, 00:46:58, Serial0/0/1
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
D 172.16.0.0/16 is a summary, 00:38:09, Null0
C 172.16.2.0/24 is directly connected, Loopback1
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
D 192.168.1.0/24 is a summary, 00:47:06, Null0
C 192.168.1.64/28 is directly connected, Loopback0
On CoreRouter
CoreRouter#sh ip route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 7 subnets, 2 masks
D 10.0.0.0/8 is a summary, 00:47:53, Null0
C 10.1.1.0/24 is directly connected, FastEthernet0/0
D 10.2.2.0/24 [90/2172416] via 10.140.1.2, 00:47:47, Serial0/0/0
D 10.3.3.0/24 [90/2172416] via 10.140.2.2, 00:47:45, Serial0/0/1
D 10.23.23.0/24 [90/2681856] via 10.140.1.2, 00:47:47, Serial0/0/0
[90/2681856] via 10.140.2.2, 00:47:45, Serial0/0/1
C 10.140.1.0/24 is directly connected, Serial0/0/0
C 10.140.2.0/24 is directly connected, Serial0/0/1
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
D 172.16.0.0/16 is a summary, 00:47:53, Null0
C 172.16.31.0/24 is directly connected, Loopback0
D 192.168.1.0/24 [90/2297856] via 10.140.1.2, 00:47:47, Serial0/0/0
[90/2297856] via 10.140.2.2, 00:47:45, Serial0/0/1
As shown in the routing tables, EIGRP has summarized the 172.16.2.0/24 and 172.16.31.0/24 networks into 172.16.0.0/16 and there is no route between these 2 networks.
Let’s disable auto-summary on both the routers and check out the routing tables again.
RouterA(config)#router eigrp 100
RouterA(config-router)#no auto-summary
CoreRouter(config)#router eigrp 100
CoreRouter(config-router)#no auto-summary
On RouterA
RouterA#sh ip route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 6 subnets
D 10.1.1.0 [90/2172416] via 10.140.1.1, 00:00:23, Serial0/0/0
C 10.2.2.0 is directly connected, FastEthernet0/0
D 10.3.3.0 [90/2172416] via 10.23.23.2, 00:04:29, Serial0/0/1
C 10.23.23.0 is directly connected, Serial0/0/1
C 10.140.1.0 is directly connected, Serial0/0/0
D 10.140.2.0 [90/2681856] via 10.23.23.2, 00:04:29, Serial0/0/1
[90/2681856] via 10.140.1.1, 00:00:23, Serial0/0/0
172.16.0.0/16 is variably subnetted, 3 subnets, 2 masks
D 172.16.0.0/16 [90/2809856] via 10.23.23.2, 00:00:23, Serial0/0/1
C 172.16.2.0/24 is directly connected, Loopback1
D 172.16.31.0/24 [90/2297856] via 10.140.1.1, 00:00:23, Serial0/0/0
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
D 192.168.1.0/24 [90/2297856] via 10.23.23.2, 00:04:29, Serial0/0/1
C 192.168.1.64/28 is directly connected, Loopback0
On CoreRouter
CoreRouter#sh ip route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 6 subnets
C 10.1.1.0 is directly connected, FastEthernet0/0
D 10.2.2.0 [90/2172416] via 10.140.1.2, 00:00:07, Serial0/0/0
D 10.3.3.0 [90/2172416] via 10.140.2.2, 00:00:07, Serial0/0/1
D 10.23.23.0 [90/2681856] via 10.140.1.2, 00:00:07, Serial0/0/0
[90/2681856] via 10.140.2.2, 00:00:07, Serial0/0/1
C 10.140.1.0 is directly connected, Serial0/0/0
C 10.140.2.0 is directly connected, Serial0/0/1
172.16.0.0/16 is variably subnetted, 3 subnets, 2 masks
D 172.16.0.0/16 [90/2809856] via 10.140.2.2, 00:00:07, Serial0/0/1
D 172.16.2.0/24 [90/2297856] via 10.140.1.2, 00:00:07, Serial0/0/0
C 172.16.31.0/24 is directly connected, Loopback0
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
D 192.168.1.0/24 [90/2297856] via 10.140.2.2, 00:00:07, Serial0/0/1
D 192.168.1.64/28 [90/2297856] via 10.140.1.2, 00:00:07, Serial0/0/0
By disabling auto-summary, both routers are exchanging subnets information. If we try the ping test again, it should work now.
RouterA#ping
Protocol [ip]:
Target IP address: 172.16.31.100
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 172.16.2.1
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.31.100, timeout is 2 seconds:
Packet sent with a source address of 172.16.2.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/3/5 ms
Automatic is not always the best!